Cloud
Top Cloud Security Challenges & How to Beat Them
The ongoing shift of traditional IT functions to the cloud brings new cyber risks for enterprises. Discover three current cloud security challenges and how to prevent them from causing financial, operational, and reputational damage.

Learn more about cloud security by joining Trend Micro at AWS re:Invent from Nov. 28 - Dec. 2
Cybersecurity Awareness Month 2022 Series
Companies continue to move traditional IT functions to the cloud for agility and flexibility. According to Gartner, more than half (51%) of all enterprise spending on application and infrastructure software, business process services and system infrastructure will be going to the cloud by 2025. While the business benefits are undeniable, this shift also brings new cloud security challenges. The Trend Micro 2022 Midyear Cybersecurity Report identified three growing trends that pose financial, operational and reputational risks to enterprises: cryptocurrency mining, cloud tunnel exploits, and cloud software misconfigurations.
Cloud security challenge 1: Cryptocurrency mining
Cryptocurrencies may have had a bumpy 2022, but they remain highly lucrative, and the anonymity they provide makes them appealing to cybercriminals, who have leapt at the opportunity to literally make money by mining new crypto coins. Because crypto mining is computationally intensive, cybercriminals are increasingly infiltrating and taking over enterprise cloud resources to boost their computing power.
What’s at risk
Unlike other kinds of breaches, cryptocurrency mining poses a relatively low reputational risk to enterprises because its primary aim isn’t to disrupt services or steal sensitive data. But it can be costly if it goes undetected, racking up charges on what are typically pay-as-you-go resources. Trend Micro estimates a cloud-based cryptocurrency mining attack can reach USD $130 per month for a single machine. Since most enterprises have multiple cloud instances, the costs can multiply quickly.
These attacks also divert computing resources away from core workloads, which can hamper productivity. And if illicit use maxes out defined quotas, then enterprise services won’t scale as they should—affecting business performance.
What enterprises can do
Because cryptocurrency mining can be done with any cloud resource, attackers often target development and staging environments, which typically have fewer protections than production environments. Weak credentials or passwords and vulnerabilities that permit remote commands are commonly exploited for these kinds of attacks.
Enterprises can extend the automated software tools they use to defend more critical resources and scan for anomalies across dev resources, too. Setting cloud cost limits and blocking non-local cloud regions can further help constrain dev environments and prevent cloud resources from being co-opted.
Cloud security challenge 2: Cloud tunnel exploits
Software and application developers often use cloud tunnels as a quick and easy way to share work in progress by temporarily exposing their local systems. As these tunnels essentially bypass restrictions on corporate network access, they make it possible for an attacker to reach through and infiltrate the dev computer.
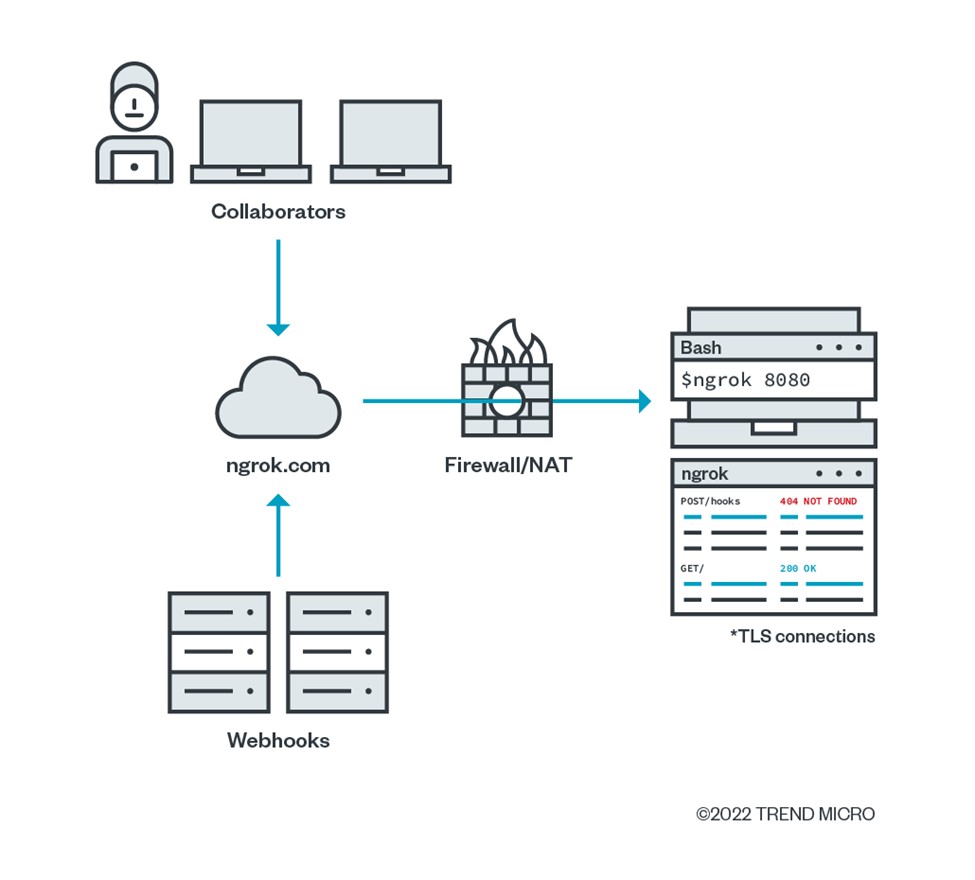
An overview of how ngrok, a cloud tunnelling service, works.
What’s at risk
With access to a developer’s machine, cybercriminals can take advantage of local admin privileges or the shared work-in-progress to seed malware. They can also use hijacked credentials to get into the organization’s cloud dev environment or other systems, potentially accessing sensitive information or injecting vulnerabilities into application source code and pipelines. These kinds of breaches are hard to detect because the associated network activity appears legitimate based on the developer’s privileges and identity.
What enterprises can do
As much as possible, organizations should configure security systems to filter outbound connections just as they do inbound ones. Since people will likely seek workarounds if barred completely from using cloud tunnels, it’s also important to set clear policies that identify what the organization considers to be necessary cloud tunneling use cases. And instead of multiple ad hoc cloud tunnels, enterprises should authorize just one, restricted to within the organization and not open to the internet.
Cloud security challenge 3: Misconfiguration exploitation
Software misconfigurations have been found to account for 65 to 70% of all cloud security challenges, with a cost to companies of nearly USD $5 trillion. A Red Hat survey noted 53% of respondents had detected a misconfiguration in their container and/or Kubernetes deployments. Part of the reason these vulnerabilities are so common is that the virtualization and cloudification of IT infrastructure has blurred traditional lines of responsibility between developers and infrastructure or security teams.
What’s at risk
Misconfigurations can take many forms, from erroneously making storage ‘world-readable’ and exposing sensitive information to improperly implementing security controls. This opens up enterprises to a wide range of potential threats: malware, data theft, hijacked repositories, arbitrary workloads (including cryptocurrency mining), and more.
What enterprises can do
Adopting good cloud security posture management (CSPM) practices is key. Doing so helps establish clear domains of responsibility, allowing security teams to set policy, and requiring application and infrastructure developers to ensure their work conforms. CSPM software tools give enterprise security teams the visibility to check and monitor cloud resources proactively for misconfigurations—catching them early and correcting them before vulnerabilities can be exploited.
A unified approach to tackling cloud security challenges
Questions of “who’s responsible?” don’t relate only to teams within the enterprise. Public cloud services require careful delineation of roles between the enterprise and cloud providers to ensure end-to-end security. In the shared responsibility model, cloud providers are responsible for the security of their infrastructure, APIs and data storage and handling in the cloud. It’s up to the enterprise to use those cloud services securely, involving multiple layers of internal roles and functions: security, cloud operations, DevOps and the like.
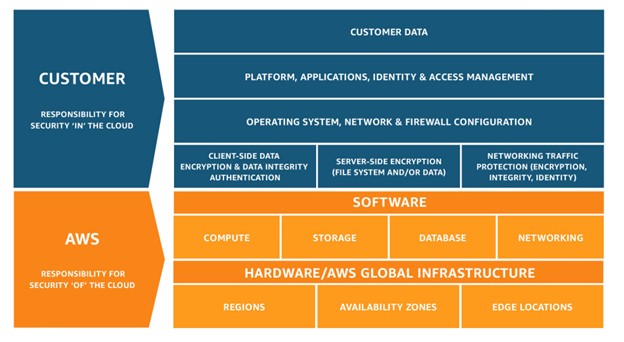
Source: Amazon Web Services
Deploying and maintaining separate security tools at each layer would be unmanageable, especially if an enterprise were to also source individual tools for workload security, container security and other functions. Having a unified security platform that covers all the environments and technologies is essential.
This is even more true in hybrid and multi-cloud situations. Using one platform across multiple environments and gaining a single, unified view of the whole radically simplifies and strengthens security. A unified platform with extended detection and response (XDR) capabilities and strong CSPM software should provide those capabilities.
Perhaps most importantly, any approach to addressing cloud security challenges needs to support—and not interfere with—the reasons enterprises are switching to the cloud in the first place. That means cloud security itself should be agile, on-demand, and available through online marketplaces, with the ability to scale right alongside enterprise cloud resources.
As enterprise use of cloud technologies will only continue to grow and diversify, establishing a unified and cloud-friendly approach to security is key. As cloud threats will also evolve over time, it is equally important for companies to follow the latest research and keep their cloud security posture up to date.
Next steps
For more insights on cloud security trends and risk management, explore these additional resources:

